Google, Bing, Yahoo, Yandex, and Baidu are some of the world’s top search engines and serve as the starting point for millions of internet users seeking information. Most people probably don’t browse past the first two or three pages of search results, which is why website owners aim to get their site to appear among the top results, to attract site visitors. Website owners do this using a process called search engine optimization (or SEO). Businesses rely on good reviews, Google Maps, and optimized content to ensure their websites are well tuned to be easily searched and shown in results.
Scammers have realized that they can also use SEO to find more victims and convince them into clicking on a link if their websites appear higher in search engine results. Using this, they are able to get well known search engines to list simple html web pages that contain redirectors leading to scam content. A typical scam page might be a simple page convincing people that they won a new iPhone and with the right search words, malicious links can be listed on the first and second pages of search results.
How?
It all starts with a simple search. If you put enough keywords into the search box, the result may include simple websites that were created just to be easily indexed and listed by the search engines. For this query below, I searched for online films with subtitles in Romanian. Our data shows a lot of activity on Google and Yandex.
 Google search results with fake product reviews
Google search results with fake product reviews
 Yandex search results
Yandex search results
All of the scam websites look similar. The only difference is the targeted brands. The source code of the website clearly shows the effort to make simple webpages as SEO friendly as possible.
 Well SEO-optimized simple website
Well SEO-optimized simple website
The simple design with only text and pictures is not meant for the users’ eyes. The purpose of this website is hidden, as always, in the source code.
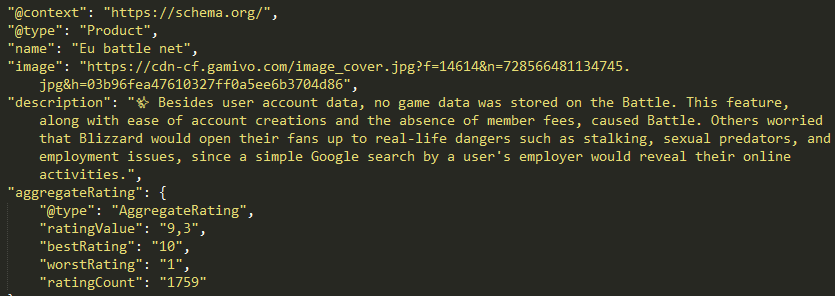 Fake rating
Fake rating
The first glance shows fixed code to create the appearance of positive Google product reviews in rich search results. The static information attached is more noticeable amongst other links in search results (show in second illustration).
The source code also shows an import of heavily obfuscated javascript which takes fingerprints of the user before redirecting them to the scam site.
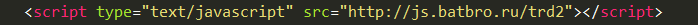 Import of obfuscated script
Import of obfuscated script
Obfuscation of the source code utilizes many cycles of functions, which essentially builds final source code word by word.
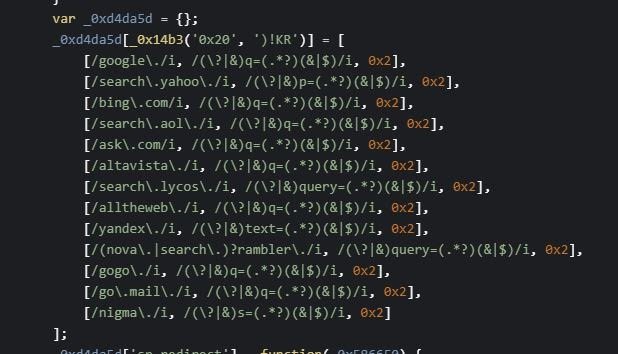 Variable BaatKw loads deobfuscated values during script evaluation
Variable BaatKw loads deobfuscated values during script evaluation
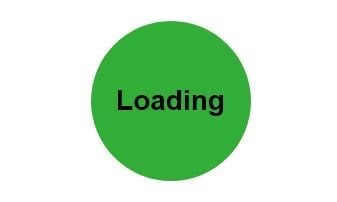
 During script evaluation users see a simple loading image
During script evaluation users see a simple loading image
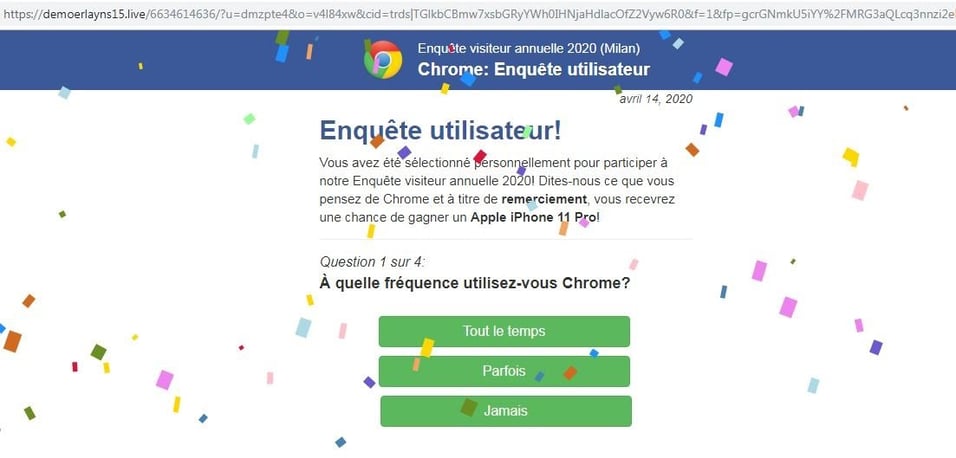
When clicking on the link in the google search results, the user, for a brief moment, sees a simple loading image before the site redirects them to one of the prepared scam websites. For example, one of the sites can be a fake questionnaire, asking you to answer a few questions to get the chance of winning the latest iPhone. Or a simple game where you open presents. We are seeing many newly registered domains whose only purpose is to host the scam content.
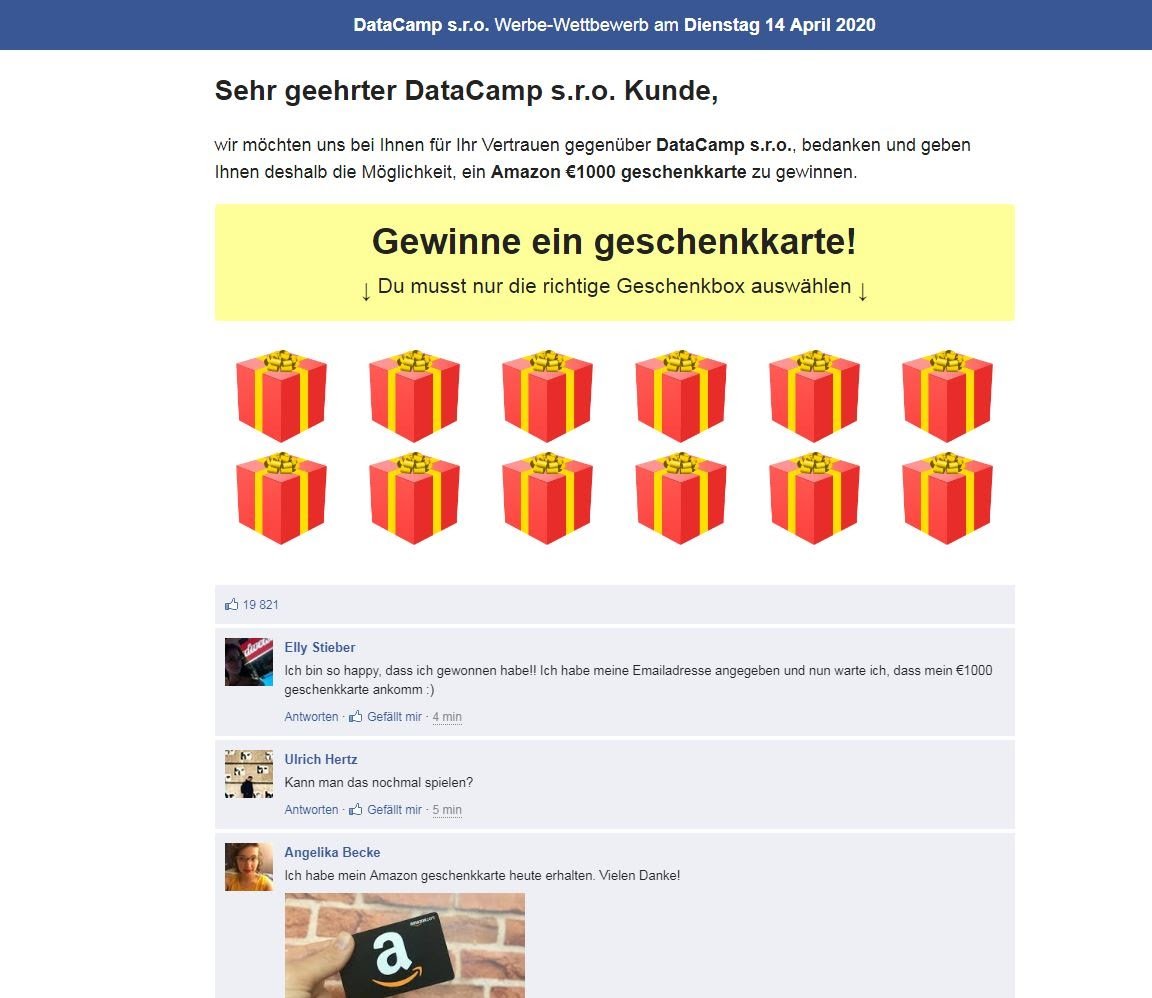 A possible scam site
A possible scam site
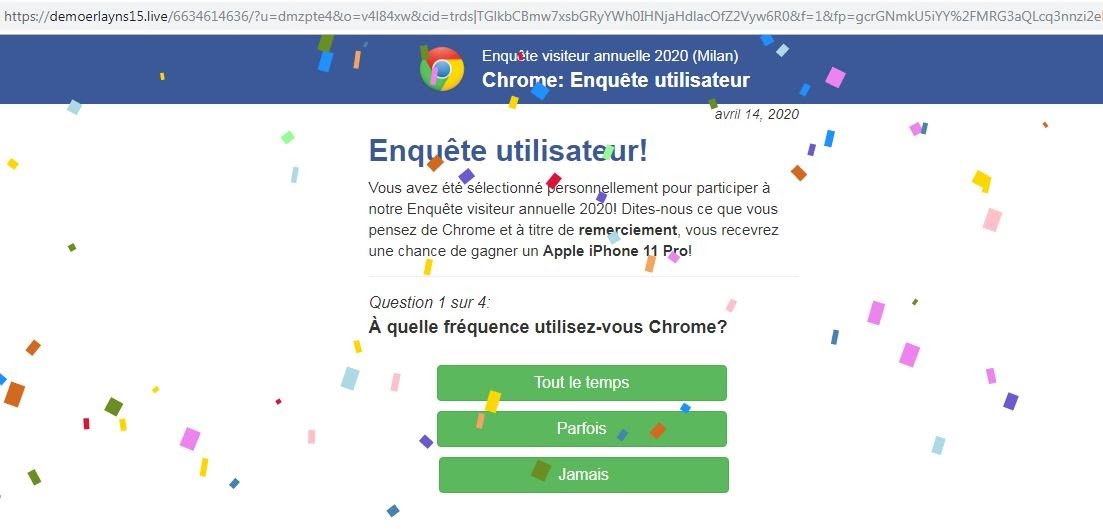 Scam questionnaire
Scam questionnaire
Resolved IP address of demoerlayns[.]live hosts more than 5k other suspicious domains.
 Whois information of demoerlayns[.]live
Whois information of demoerlayns[.]live
If you tried to visit some of those domains, the typical return is blank page with a note.
 Main page
Main page
But adding the correct parameter, you get scam content.
 Susp domain with parameter
Susp domain with parameter
 Other suspicious domain resolving on same IP address
Other suspicious domain resolving on same IP address
 Hundreds of newly occurred domains on resolved IP
Hundreds of newly occurred domains on resolved IP
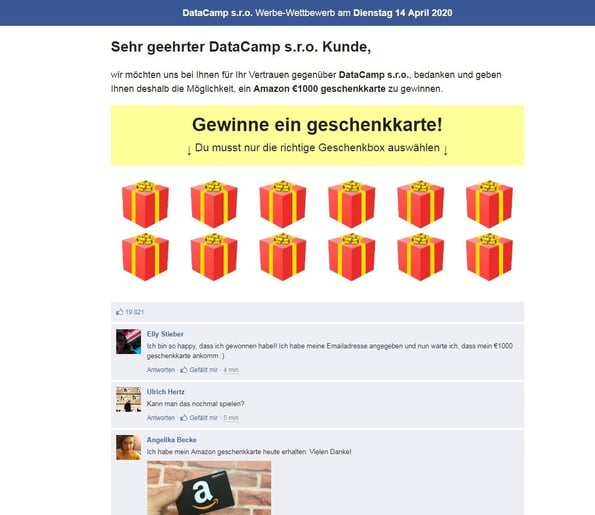
But back to the scam page itself. After answering all of the questions, the website acts as if it is evaluating answers and then, surprise, surprise, you are the winner. To help convince those who are already a bit suspicious of the offers, there are several fake Facebook comments where users comment about their new phones. All of the text on this page is translated to Czech or other languages, depending on where your IP address is, without noticeable grammatical errors.
 Fake comments
Fake comments
So you won. Now what? In order to get your prize, all you have to do is click on the provided link set up to convince the user that there is apparently only one left. This click will transfer you to another webpage.
Fake page offering prize for a small fee
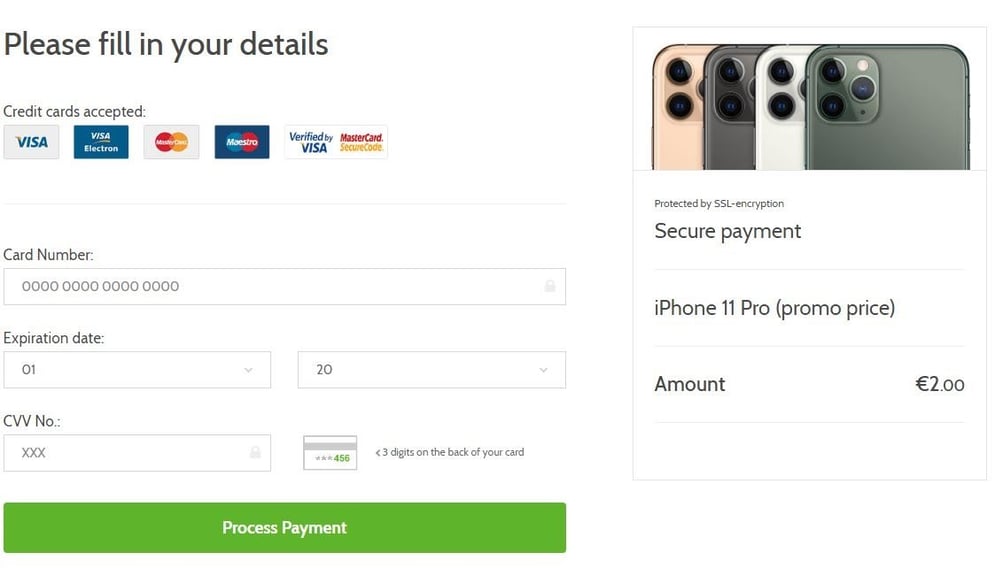
A simple but nicely designed form comes up with the option to pick the color of your new device. The only thing left to do is fill out your contact information and pay a symbolic price of 2 euros. There are several designs that come up of essentially the same page.
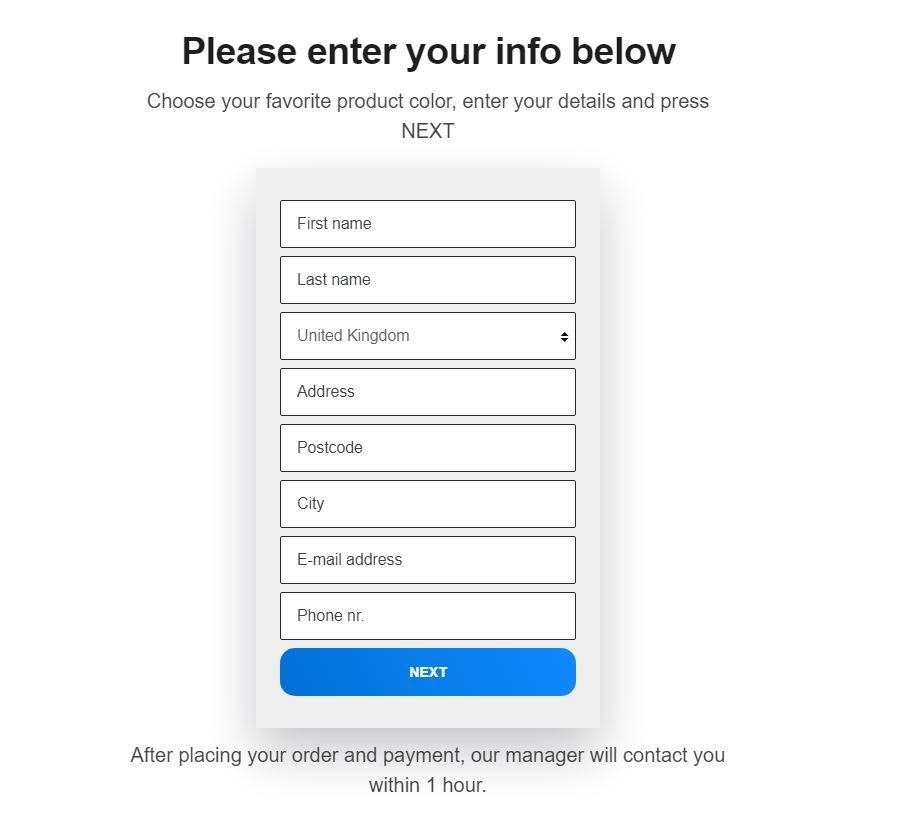 One of the possible payment sites
One of the possible payment sites
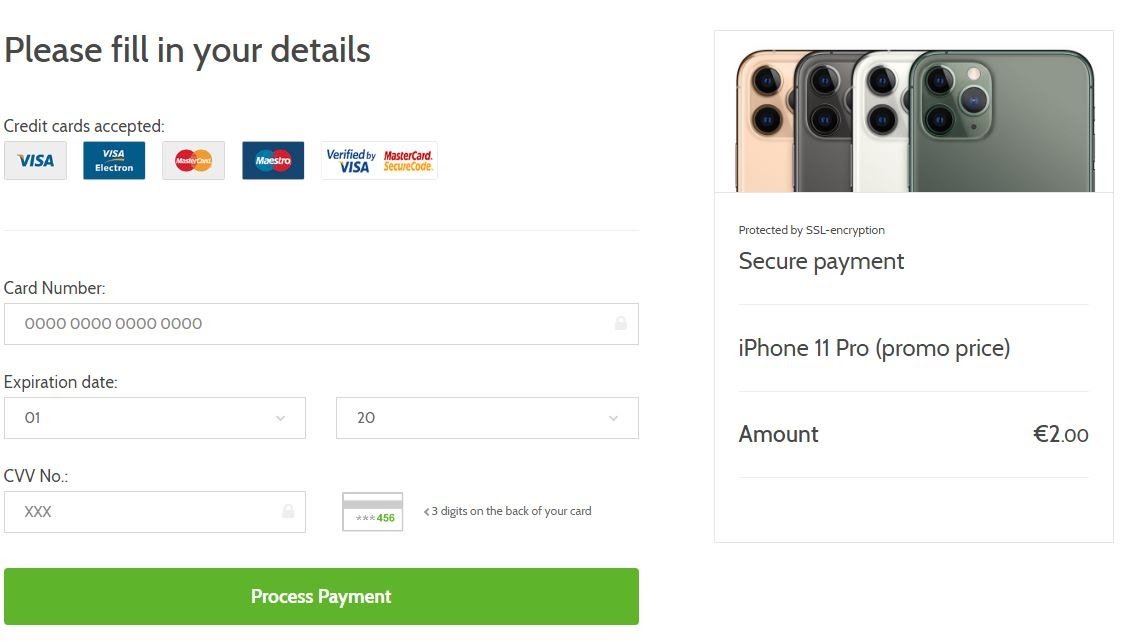 Payment form
Payment form
This ends with the user sending your money to the attackers and the user assuming they almost have a free iPhone. Although this is the common scam, there are variants. You can end up with a page asking you to allow push notifications. By allowing those notifications, your browser will start showing you unwanted ads, shown below.
 Push notification pop-up
Push notification pop-up
 Unwanted ads in notifications
Unwanted ads in notifications
Another one of these scam variants that attackers have made is a different website promising solutions for those who want to earn big money, continuing on the lines to help people, by having them make a payment in order to receive more.
 More scam variants
More scam variants
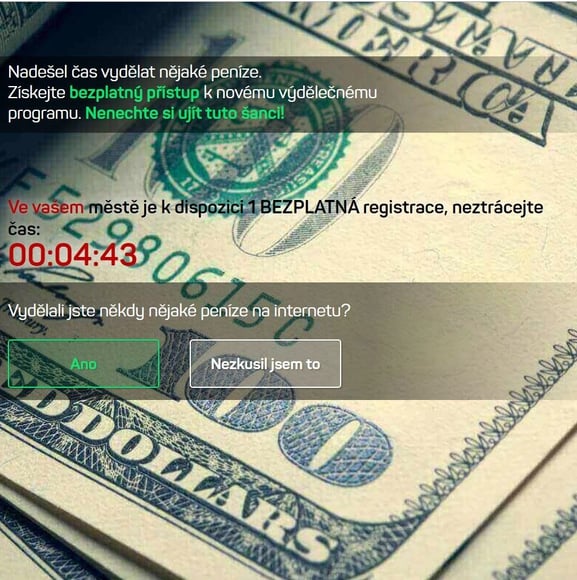 Other possible category of scam
Other possible category of scam
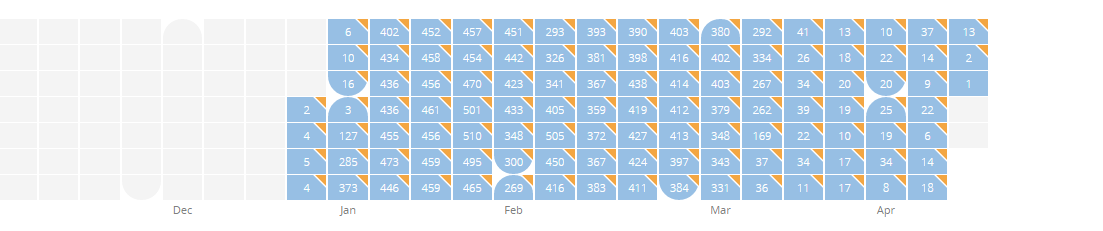
From what we are seeing in our data, these types of scam campaigns are growing in popularity. In comparison with phishing campaigns, where it is easier to analyze and find these campaigns by the source code, these kinds of scam website campaigns can give attackers not only users credentials, but are often also monetized. A lot of these campaigns use large amounts of targeting before showing this particular content to users. This affords them a better chance to avoid detections by antivirus software. If you’re searching online for something specific and you come across an offer that seems too good to be true, it probably is. Be careful about who you are sharing your financial information with online and don’t fall prey to these types of scams.
 Scam campaign has a global focus (As of June 8th)
Scam campaign has a global focus (As of June 8th)
As you can see in the illustration, our data shows that the detected campaign has a global impact.